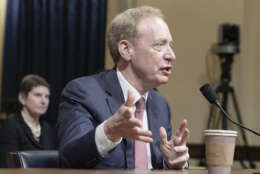Hubbard Radio Washington DC, LLC. All rights reserved. This website is not intended for users located within the European Economic Area.
Cybersecurity Month
Sponsored by


This is the 17th year of Cybersecurity Awareness Month and Kevin Harris, cybersecurity program director at American Military University, says a lot has changed since those early days.
Read moreThe Defense Information Systems Agency moved its cloud based internet isolation program into production after testing it out for the last year under a $199 million Other Transaction Agreement.
David Waltermire, the technical lead for OSCAL at NIST, and Milica Green, a compliance subject matter expert with Telos Corporation, say the development and implementation of the Open Security Controls Assessment Language (OSCAL) will reduce the time, cost and challenges of FedRAMP certifications.
Cynthia Mendoza, the intelligence community’s chief architect, said the reference architecture framework is defining consistent, repeatable approaches to ensure security and interoperability among enterprise IT capabilities.
-
DHS names China, AI, cyber standards as key priorities for critical infrastructure
Agencies that oversee critical infrastructure are developing new sector risk management plans, with cybersecurity continuing to be a high priority.
-
Robust data management is key to harnessing the power of emerging technologies
Comprehensive data management is key to unlocking seamless, personalized and secure CX for government agencies.
-
Energy working with renewables industry, cloud providers on cyber requirements
CESER’s work with cloud service providers comes amid growing threats to critical infrastructure, as well as questions about cloud security responsibilities.
-
NSF initiative aims to bring better data to the cyber workforce challenge
Policymakers often talk about a cyber talent gap, but official data on the national cyber workforce is also in short supply.
-
Some feds continue to see fraudulent FSAFEDS deductions
One former official questioned why OPM and the FSAFEDS program didn’t have stronger fraud controls in place before recent reports of fraudulent deductions.
-
Four key highlights from the Microsoft cybersecurity hearing
Microsoft President Brad Smith made a number of key commitments, but faced no harsh criticism for his company’s documented cybersecurity shortcomings.
-
Elevating visibility: The stabilizing force in responsive cyber defense
Agencies need a threat-informed defense approach that leverages global adversary signals and early warning capabilities to defend against cyber threats.
-
How the Army is always testing, training on zero trust
The Army I Corps used the recent Yama Sakura 85 exercise to further prove out how to create a single, secure network to share information with allied partners.